Lenovo is selling computers that bring already pre-installed software that hijacks your browser encrypted sessions putting the user vulnerable to man-in-the-middle attacks (HTTP).
This attack can, for example, to obtain user credentials in access to online banking, even with an encrypted HTTPS session.

The Chinese company placed on their computers software that would serve to “shoot” in the browser of any user an advertising page. However, this decision proved to be a threat to any PC.
Lenovo PCs have installed adware from a company called Superfish. This type of advertising is unpleasant for any user because injects advertising on Web pages that hate the user. But the worst is that the Superfish also install a certificate of self-signed HTTPS root, allowing all browser traffic, including what comes encrypted, such as access to their bank, can be held hostage to the software.
& amp; NBPs;
How does the technique
When a user visits a HTTPS site, the site’s certificate is signed and verified by Superfish? , thus pass up as the certificate of the official website.
But, more seriously, is that the private key that accompanies the signed certificate Superfish Transport Layer Security always seems to be the same on each machine Lenovo.
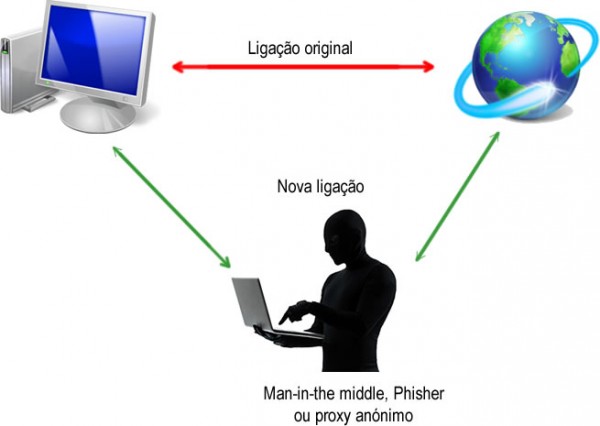
Thus, attackers can use this key certified to masking of Google, your bank or any other destination safe on the Internet.
In this scenario, the computers that have the root certificate installed Superfish will have a “security hole” that involves your whole life HTTPS secure protocol.
New this adware?
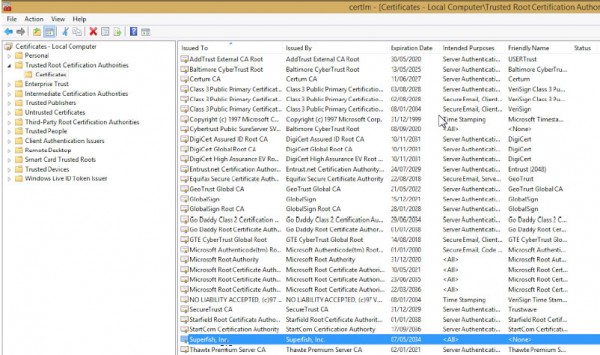
Apparently, this threat have much time left. The subject adware and its effect on the Web encryption has already being discussed on various topics related to Lenovo. . Since last September that the Lenovo forum there are already complaints as we can see here and here
In the last post, dated January 21, a user showed a root certificate with the Superfish name that was installed:
Once installed, the script went on to show himself as being a certified tampered with the HTTPS connection if transfigured into a banking site, behavior that allowed the Superfish collect all the unencrypted data.
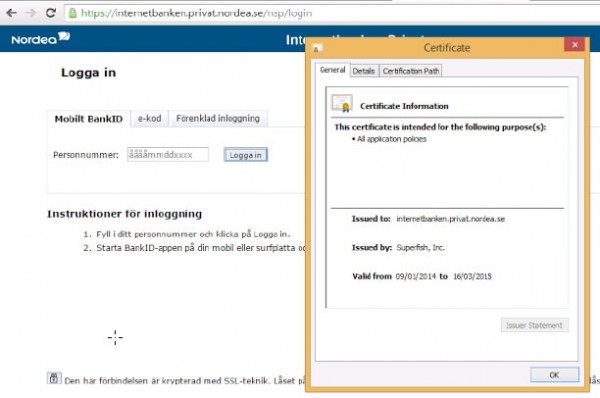
Surprisingly, the behavior escaped the watchful eye of defenders privacy and security, at least so far. On Wednesday evening, after several Twitter lengthy discussions about this behavior, the security researcher Chris Palmer bought a Lenovo Yoga 2 Pro for $ 600 in a Best Buy store in San Francisco Bay. Quickly, confirmed that the model was pre- installed with Superfish software and with a self-signed key.
When Palmer visited https://www.bankofamerica.com/ site, he found that the certificate presented to your browser has not been signed by VeriSign certificate authority, as expected, but by Superfish.
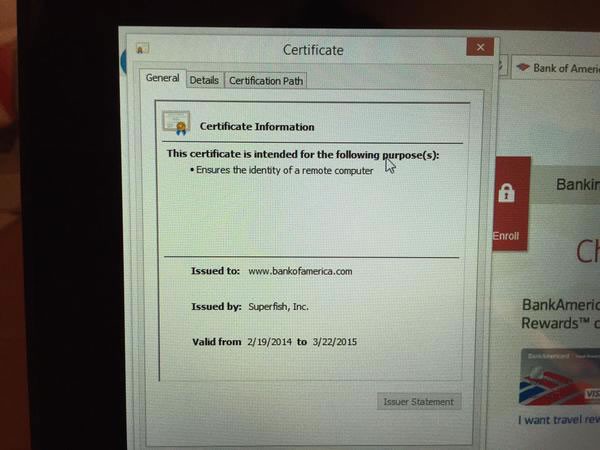
He saw the same certificate signed Superfish tampered with when he visited other sites protected by HTTPS. In fact, not a single site protected by TLS which would not be affected.
The company has responded, through a thread on their forum where you can read that due to some complaints against the browser behavior, the company decided to remove the add-on Superfish. Thus, the new machines that will go out to the market no longer bring this adware software, however for machines already on the market with this software, Lenovo asked the Superfish to launch an update. Thus, the problem will be solved and the add-on disabled.
Although the company insists that the Superfish is a software to find and discover products, the truth is that there is an engineering through the middle to break a rule security, jeopardizing the user’s own protection in a very sensitive issue in safe Internet browsing.
After this position, the company released a document with all the instructions to remove the Superfish machines already in market. In addition, this tool also removes the certificate used to deceive the https security protocol
There are several machines affected by this adware system that were placed on the market between September and December 2014:.
G Series: G410, G510, G710, G40-70 , G50-70, G40-30, G50-30, G40-45, G50-45
U Series: U330P, U430P, U330Touch, U430Touch, U530Touch
Y Series: Y430P , Y40-70, Y50-70
Z Series: Z40-75, Z50-75, Z40-70, Z50-70
S Series: S310, S410, S40-70 , S415, S415Touch, S20-30, S20-30Touch
Flex Series: Flex2 14D, 15D Flex2, Flex2 14, Flex2 15, Flex2 14 (BTM), Flex2 15 (BTM), Flex 10
MIIX Series: MIIX2-8, MIIX2-10, MIIX2-11
Yoga Series: YOGA2Pro-13, YOGA2-13, YOGA2-11BTM, YOGA2-11HSW
E Series: E10-30
<- 123 281 767 321 ->
<-
No comments:
Post a Comment